Vulnerability Management: Vulnerability Export Open Port Findings for Info-level Plugins
On October 11, 2023, customers that enabled the Relocate Open Port Findings setting in the user interface will see a data structure change in their vulnerability exports for open ports reported by the following high-traffic info plugins:
- 34220 — Netstat Portscanner (WMI)
- 34252 — Microsoft Windows Remote Listeners Enumeration (WMI)
- 11219 — Nessus SYN Scanner
- 14272 — Netstat Portscanner (SSH)
- 25221 — Remote listeners enumeration (Linux / AIX)
- 99265 — macOS Remote Listeners Enumeration
- 10335 — Nessus TCP scanner
- 14274 — Nessus SNMP Scanner
- 34277 — Nessus UDP Scanner
Currently, the open port findings from these plugins are provided as individual findings. When the new Relocate Open Port Findings setting is enabled, the open port findings will be aggregated and available as a single finding. Refer to the following examples for details about this data structure change.
For more information about open ports reported by info-level plugins and the Relocate Open Port Findings setting, see Relocate Open Port Findings in the Tenable Vulnerability Management User Guide and the Relocate Open Port Findings Quick Reference Guide.
Currently, when you perform a vulnerability export via the API, open port findings are provided as individual findings. Each finding contains data for only one open port. For example, see the following individual vulnerability finding, the relevant portions are highlighted in red.
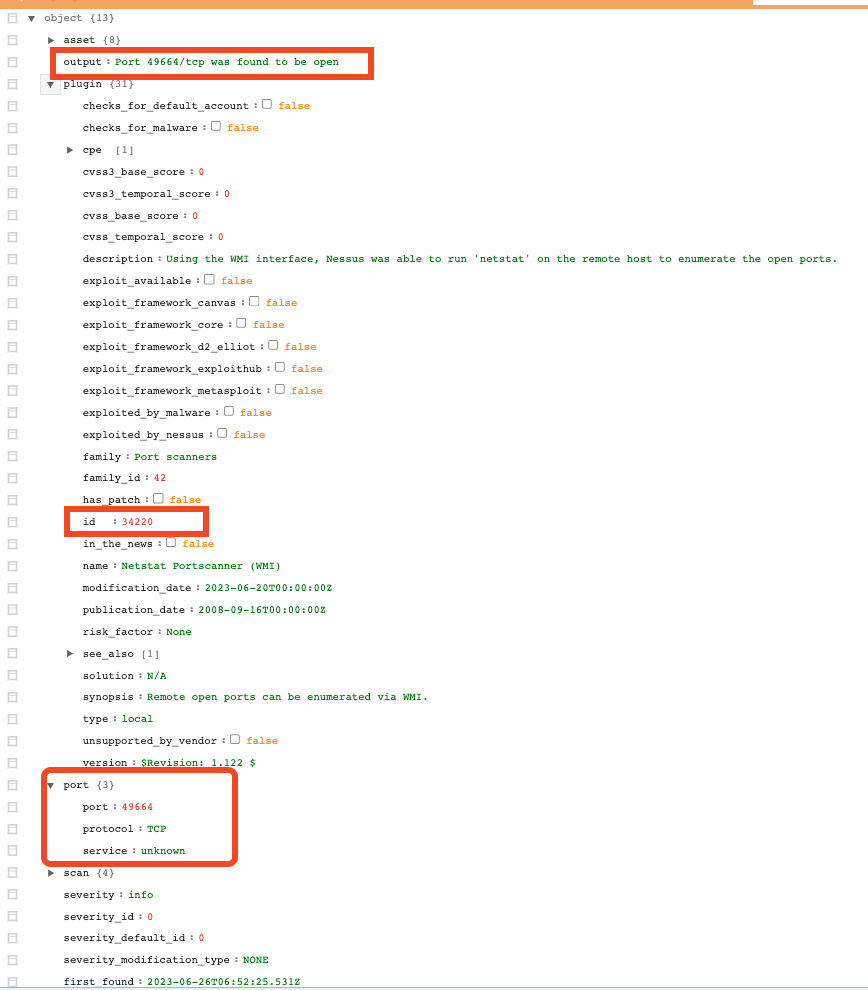
The following snippet contains a raw JSON response:
{
"asset": {
"agent_uuid": "dc488f7cc7cb48098bd9a32bce2100b8",
"fqdn": "denise.ad.demo.io",
"hostname": "192.168.16.128",
"uuid": "37c8f0a8-c1d5-4780-b19f-0944c9dad1b8",
"ipv4": "192.168.16.128",
"netbios_name": "DENISE",
"network_id": "00000000-0000-0000-0000-000000000000",
"tracked": true
},
"output": "Port 49664/tcp was found to be open",
"plugin": {
"checks_for_default_account": false,
"checks_for_malware": false,
"cpe": [
"cpe:/o:microsoft:windows"
],
"cvss3_base_score": 0.0,
"cvss3_temporal_score": 0.0,
"cvss_base_score": 0.0,
"cvss_temporal_score": 0.0,
"description": "Using the WMI interface, Nessus was able to run 'netstat' on the remote host to enumerate the open ports.",
"exploit_available": false,
"exploit_framework_canvas": false,
"exploit_framework_core": false,
"exploit_framework_d2_elliot": false,
"exploit_framework_exploithub": false,
"exploit_framework_metasploit": false,
"exploited_by_malware": false,
"exploited_by_nessus": false,
"family": "Port scanners",
"family_id": 42,
"has_patch": false,
"id": 34220,
"in_the_news": false,
"name": "Netstat Portscanner (WMI)",
"modification_date": "2023-06-20T00:00:00Z",
"publication_date": "2008-09-16T00:00:00Z",
"risk_factor": "None",
"see_also": [
"https://en.wikipedia.org/wiki/Netstat"
],
"solution": "N/A",
"synopsis": "Remote open ports can be enumerated via WMI.",
"type": "local",
"unsupported_by_vendor": false,
"version": "$Revision: 1.122 $"
},
"port": {
"port": 49664,
"protocol": "TCP",
"service": "unknown"
},
"scan": {
"completed_at": "2023-06-26T06:52:25.531Z",
"schedule_uuid": "893c856a-278f-41e0-8c5a-d33ea82f6784",
"started_at": "2023-06-26T06:52:25.531Z",
"uuid": "1875cce9-c964-5195-f829-d47a990c059c2297fdcc4ec0cc09"
},
"severity": "info",
"severity_id": 0,
"severity_default_id": 0,
"severity_modification_type": "NONE",
"first_found": "2023-06-26T06:52:25.531Z",
"last_found": "2023-06-26T06:52:25.531Z",
"state": "OPEN",
"indexed": "2023-06-26T08:25:46.502090Z"
}
When the Relocate Open Port Findings setting is enabled, the open port findings are aggregated and available as a single finding. For example, see the following individual vulnerability finding, the relevant portions are highlighted in red.
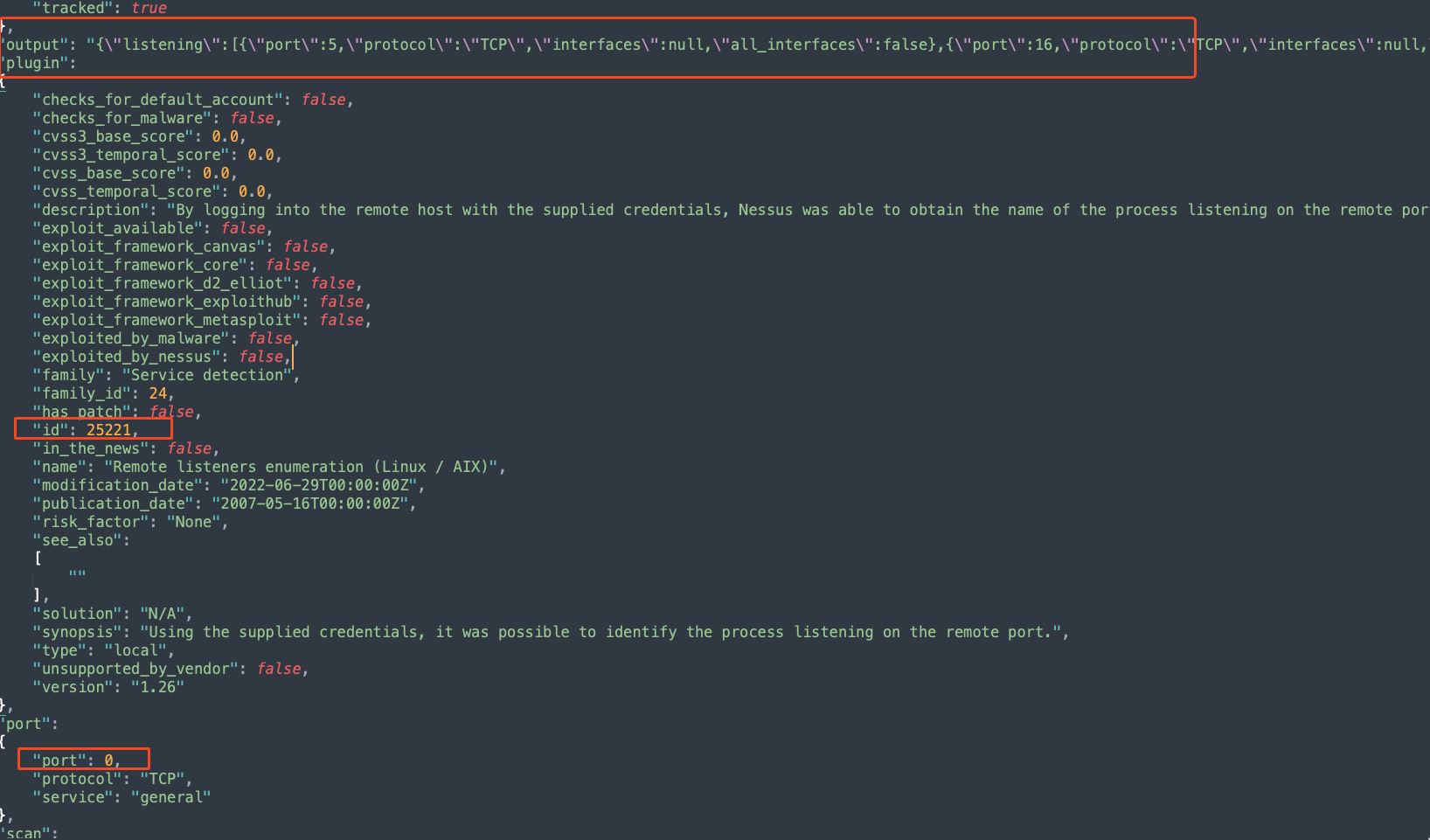
The following snippet contains a raw JSON response:
{
"asset": {
"device_type": "Endpoint",
"fqdn": "44.154.190.121.e2e.com",
"hostname": "44.154.190.121",
"uuid": "54a944cc-890d-4744-96e0-81ec94f0e943",
"ipv4": "44.154.190.121",
"last_unauthenticated_results": "2022-05-31T09:08:14Z",
"operating_system": [
"Windows"
],
"network_id": "00000000-0000-0000-0000-000000000000",
"tracked": true
},
"output": "{\"listening\":[{\"port\":5,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":16,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":26,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":36,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":46,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":56,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":66,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":76,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":86,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":96,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":106,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":117,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":128,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":139,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":150,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":161,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":172,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":183,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":194,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":205,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":216,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":227,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":238,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":249,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":260,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":271,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":282,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":293,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":304,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":315,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":326,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":337,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":348,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":359,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":370,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":381,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":392,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":403,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":414,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":425,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":436,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":447,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":458,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":469,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":480,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":491,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":502,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":513,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":524,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":535,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":546,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":557,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":568,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":579,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":590,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":601,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":612,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":623,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":634,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":645,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":656,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":667,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":678,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":689,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":700,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":711,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":722,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":733,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":744,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":755,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":766,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":777,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":788,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":799,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":810,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":821,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":832,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":843,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":854,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":865,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":876,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":887,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":898,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":909,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":920,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":931,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":942,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":953,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":964,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":975,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":986,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":997,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":1008,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":1019,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":1030,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":1041,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":1052,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":1063,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":1074,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false},{\"port\":1085,\"protocol\":\"TCP\",\"interfaces\":null,\"all_interfaces\":false}],\"closed\":{}}",
"plugin": {
"checks_for_default_account": false,
"checks_for_malware": false,
"cvss3_base_score": 0.0,
"cvss3_temporal_score": 0.0,
"cvss_base_score": 0.0,
"cvss_temporal_score": 0.0,
"description": "By logging into the remote host with the supplied credentials, Nessus was able to obtain the name of the process listening on the remote port.\n\nNote that the method used by this plugin only works for hosts running Linux or AIX.",
"exploit_available": false,
"exploit_framework_canvas": false,
"exploit_framework_core": false,
"exploit_framework_d2_elliot": false,
"exploit_framework_exploithub": false,
"exploit_framework_metasploit": false,
"exploited_by_malware": false,
"exploited_by_nessus": false,
"family": "Service detection",
"family_id": 24,
"has_patch": false,
"id": 25221,
"in_the_news": false,
"name": "Remote listeners enumeration (Linux / AIX)",
"modification_date": "2022-06-29T00:00:00Z",
"publication_date": "2007-05-16T00:00:00Z",
"risk_factor": "None",
"see_also": [
""
],
"solution": "N/A",
"synopsis": "Using the supplied credentials, it was possible to identify the process listening on the remote port.",
"type": "local",
"unsupported_by_vendor": false,
"version": "1.26"
},
"port": {
"port": 0,
"protocol": "TCP",
"service": "general"
},
"scan": {
"completed_at": "2023-07-11T13:07:48.026Z",
"schedule_uuid": "6303d6db-d49b-4990-803e-0beb9d1c6ada",
"started_at": "2023-07-11T13:07:48.026Z",
"uuid": "07482927-86e4-e704-bf03-75e42c893d69236a321d8f61bcc6"
},
"severity": "info",
"severity_id": 0,
"severity_default_id": 0,
"severity_modification_type": "NONE",
"first_found": "2023-07-11T13:07:48.026Z",
"last_found": "2023-07-11T13:07:48.026Z",
"state": "OPEN",
"indexed": "2023-07-11T13:10:31.301271Z"
}
